; Date: Mon Jun 05 2017
Tags: Russia »»»» Social Media Warfare »»»» Election Hacks »»»»
While it's widely reported that Russians built a social-media-warfare system which they're using to undermine elections in the USA and elsewhere, The Intercept has been yelling loudly "not so fast" because the allegations of Russian interference aren't verified. If we want to accuse another government of hacking our elections, or those of Moldova or Bulgaria or Montenegro or France or other countries, there'd better be solid proof, if only because the consequence of such an accusation is a possible war. Today, The Intercept (the news site that's been calling for caution) released an explosive report detailing an effort by Russian Intelligence services to directly hack into USA election systems. They were anonymously handed a top-secret NSA report, that they've analyzed and verified, detailing NSA's documentation of a "Spear-Fishing" attack launched by Russian operatives against election agencies around the country. The goal appeared to be interfering with voter registration confirmation systems. It's not known whether the attack was successful, just that it occurred.
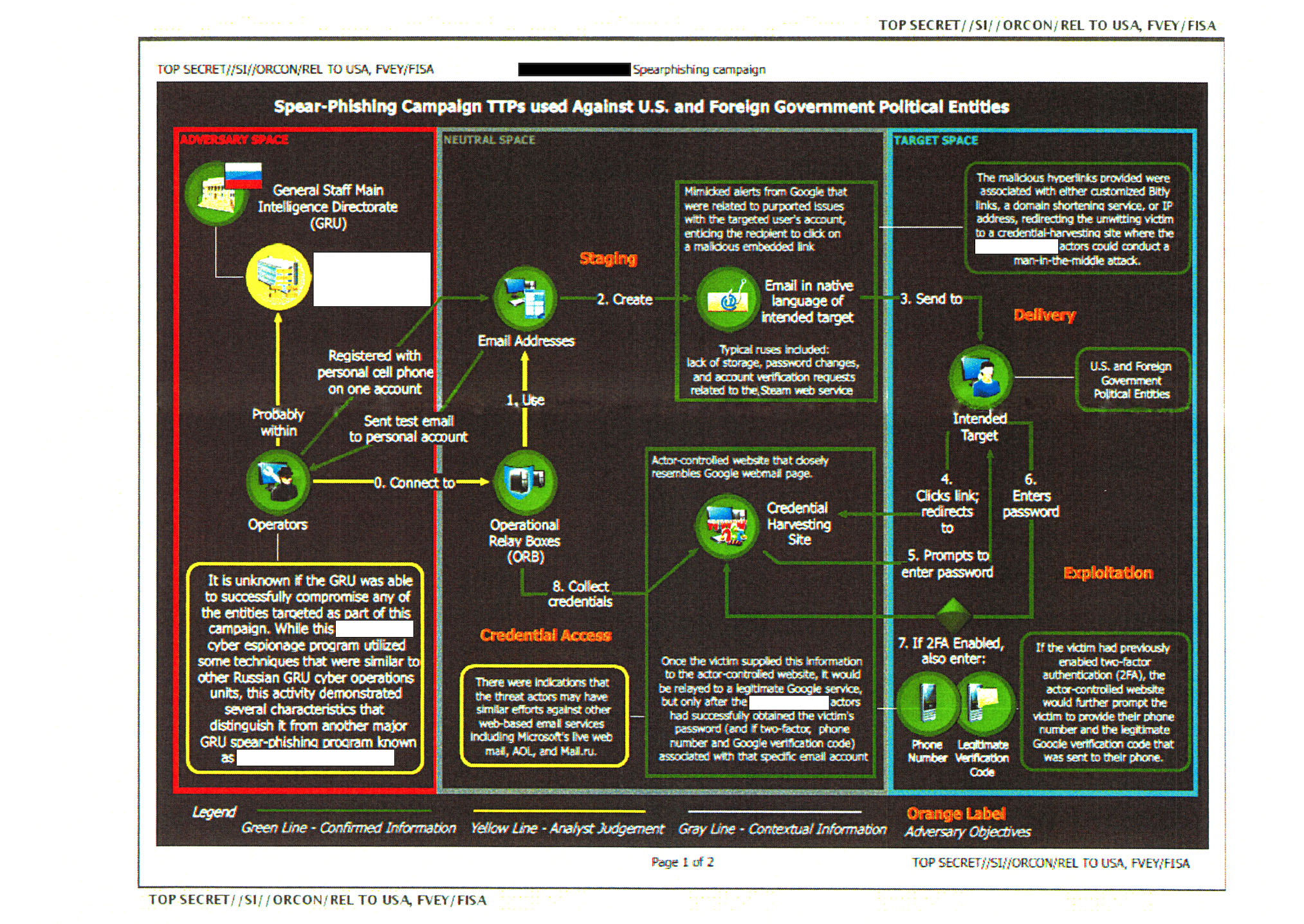
The NSA report was posted by The Intercept to Document Cloud, and is titled "Russia/Cybersecurity: Main Intelligence Directorate Cyber Actors ######BLOCKED####### Target US Companies and Local US Government Officials Using Voter Registration-Themed Emails, Spoof Election-Related Products and Services, Research Absentee Ballot Email Addresses; August to November 2016"
That title says quite a bit about the plan. Basically, Russian agents set up systems that spoofed legitimate Google services in order to harvest email addresses. Later actions included sending virus-laden MS-Word documents that purported to contain a user manual for voter registration software. The virus caused download of other malware that then gave hackers access to download pretty much any available data file.
The idea was simple - pose as a vendor of e-voting software and contact government employees. With the malware installed on government employee computers, they'd have access to data files related to the electronic voting system.
According to security experts quoted by The Intercept, if the attack had been successful the attackers would have had access to pretty much any data on the victims computer or the local network storage systems it's attached to. The only limit would be on how the network administrator configured the systems.
But: “It is unknown,” the NSA notes, “whether the aforementioned spear-phishing deployment successfully compromised the intended victims, and what potential data could have been accessed by the cyber actor.”
The target, voter registration systems, was apparently picked because they're less conspicuous than the actual voting systems. Having access to a state's voter registration system would give the ability to change voter registration status, and perhaps prevent voters from voting.
UPDATE: The NY Times says that the leaker of this report has been arrested. The Intercept had approached the NSA with questions to validate the document, and showed it to the NSA, who determined it had been printed, then folded, and hand-carried out of a secure facility. This clue narrowed down the leaker to one of six people, one of whom had been in email contact with The Intercept. That's the person who has been arrested and charged under the Espionage Act.











