; Date: Wed Apr 18 2018
Tags: Facebook »»»» Social Media »»»»
Buried in the Facebook user settings area is a page showing the permissions that have been granted to 3rd party applications. Most of us click through the permissions granting process - we just want to get to that game or whatever, and it's like a click-through-license that nobody ever reads. But recent events in Facebook's ecosystem shows the extreme danger of information leakage, of personal identifying data, from being too liberal with permissions grants. It's extremely useful that Facebook is calling attention to the permissions grants.
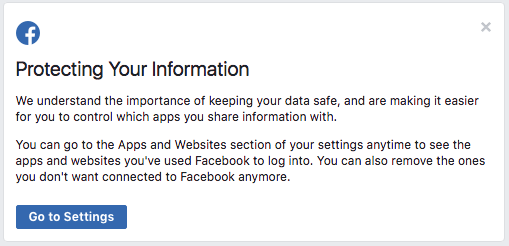
The above image appeared in my Facebook feed this morning. I would have just ignored it, but I know that this is incredibly important, and I wanted to see what's up.
If you don't get that notification, go to -- https://www.facebook.com/settings?tab=applications
In the Expired tab you'll see more applications that you, at some time, approved, but you did not use the application in so long that the tokens have expired. The service is able to renew the tokens as needed. After reviewing your active applications, its worthwhile to also review the expired applications.
Final note is that removing the application, and closing the account, once is useful. It's even more useful to make a habit of renewing this section of your Facebook settings to screen the applications. It's so easy to go through the approval process that you can easily build up quite a few approved applications, and even re-approve an application you'd previously removed.
The second final note is that other services like Twitter or Google or Github also have a similar list of approved applications. You'll need to hunt around the service user interface to see the permissions you've granted on those other services.
The following screenshots are collected from my personal account, with a few details blurred out.
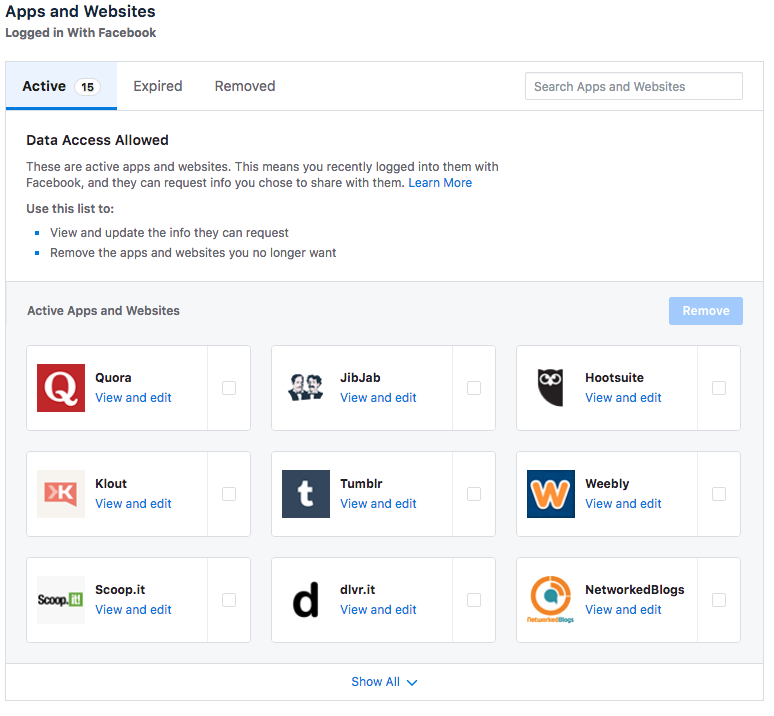
This shows some of the 3rd party applications where I've approved access to my account.
For each of these - I've clicked on a button to Login With Facebook or an equivalent. Clicking on the button caused an OAuth process to occur, where an approval was generated, and cryptographically signed authentication tokens were given to that 3rd party.
WHen the 3rd party wants to access my account - presumably to do some action on my behalf - it uses those tokens.
See: Facebook, OAuth authorization protocol, user responsibility, Facebook responsibility

This screen is a must-read because it describes just how much of your information was requested by the 3rd party application.
The Facebook API's give 3rd party app developers access to information. The access request is disclosed when you sign into the application using Facebook credentials. From a legal standpoint that means you've been notified of the information request. However, as I said, I believe most of us just click through that screen without paying attention.
In this case they requested full access to my friends list, my e-mail address, and my profile. That's a fair amount of data and I'm not entirely clear why they need that much data.
Access to the friends list can be used for viral marketing efforts - that the service might turn around and send invitations to all my friends, or offer to send postings to my friends. That's somewhat legitimate because I might well want my friends to receive things from this service.
However - the service is receiving friends lists for every every user of the service. That means the service could correlate the friends of all its users in order to create a map of connections. Is there a legitimate business purpose for that? No. But, it's informatioon a spy agency might want to collect in order to spy on us more effectively or to find known associates of known miscreants because those assoicates might also be miscreants.
What if you got a friend request from some random Facebook user - I get these all the time - and that person later turns out to cause some havoc. The FBI or someone might start scrutinizing the Facebook friends of that person to try and find associates. That means you'll come under Official Scrutiny just because you responded to a random friend request.
At the bottom of this screen is some important links. For some reason they're grey and hard to see. I've put a red box around them so be on the lookout.
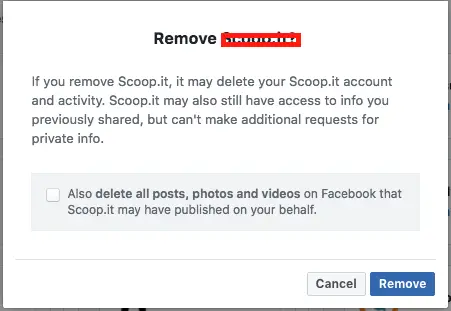
In this case I wanted to remove a few apps. In each case it was a service where I signed up, thinking it might be a useful service, and then later deleted the account on the service website. Facebook, however, still had this as an active application even though I'd deleted the account.
Hurm. Somethings wrong with that.
Before removing the app here, it's worthwhile going to the 3rd party application website and attempting to delete the account on that service.
AFTER DOING THAT, you should come back here and remove the application. One affect of removing the application is that the tokens will be revoked. By itself revoking the tokens given to the 3rd party will revoke their access.
The reason to take the extra step to delete the account is -- if the 3rd party does the right thing with data retention, it will then delete all data it collected from you.
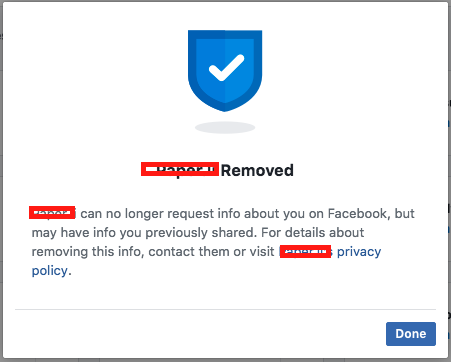
After agreeing to revoke the application, Facebook gives you this notification.











