; Date: Tue Mar 20 2018
Tags: Facebook »»»» Social Media Warfare »»»»
The firestorm around data collection by Cambridge Analytica from Facebook users is about the OAuth protocol, the required notification of access requirements, and whether Facebook actually enforces those requirements. During the OAuth protocol it's required to present the user with a screen describing the level of access requested. Facebook signed an order with the Federal Trade Commission in which Facebook agreed to abide by policies about sharing user data. Facebook may have violated that agreement. Most people don't pay attention to the notifications in the OAuth signup process. It's likely that the users abdicated their responsibility to make good decisions. Instead they, like lemmings, collectively have played the many zillions of viral games that are shared onto Facebook. It is through such games that marketers and political manipulators alike gather user preference information. Let's take a look at that process.

Mozilla just sent out a fundraising letter calling for donations, saying:
The headlines speak for themselves: Up to 50 million Facebook users had their information used by Cambridge Analytica, a private company, without their knowledge or consent. That's not okay.
This wasn't a data breach, no one hacked into Facebook or stole passwords. It happened because Facebook allowed apps to access not just sensitive information of people who used those programs – but their friends as well.
Facebook said it’s taken steps to “limit developer access to detailed friend data”, but Facebook’s current default settings leave a lot of questions and a lot of data flying around. One thing is clear though: Facebook needs to step up and respect its users.
I don't think it's accurate to say that users were not notified. The OAuth protocol -- as we will see in a second -- includes a step in which the users ARE notified as to what's going on. The problem is that it's like click-through licenses that none of us ever read.
As we said in an earlier posting Cambridge Analyticas abuse of Facebooks data causing worldwide outrage at Facebook, Facebook and the FTC came to an agreement in 2011 about Facebook's practices in this area.
For example - data retention time-limits were ignored by Cambridge Analytica. Other Facebook policies were ignored by the company, and in fact the whole process of how Cambridge Analyitica got the data was in voliation of Facebook policies.
Cambridge Analytica had turned to a third party who did the data collection. Facebook noticed that this company was doing so, and the company responded its purpose was simple research. Facebook said 'Fine' and they all went about their business. What happened next is that company sold the collected data to Cambridge Analytica in violation of policies. But we're getting off track, which is to be looking at the OAuth protocol.
Examining the OAuth protocol
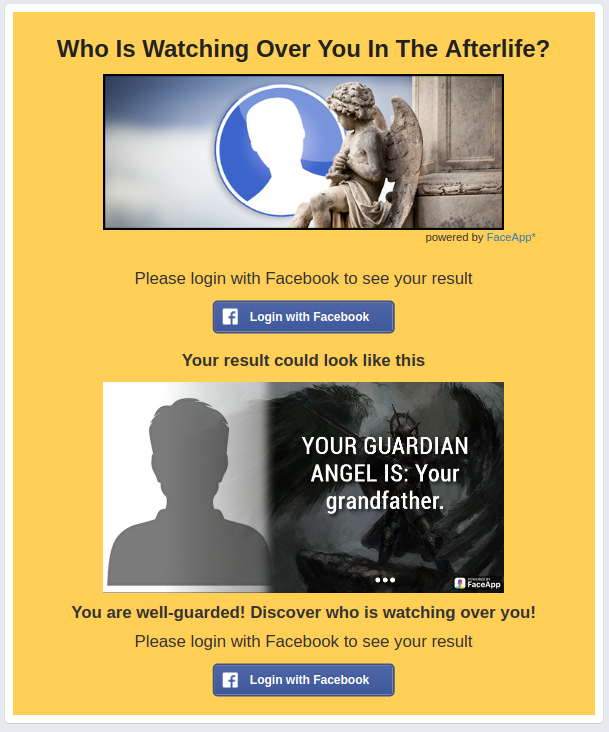
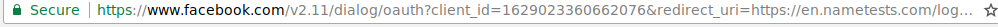
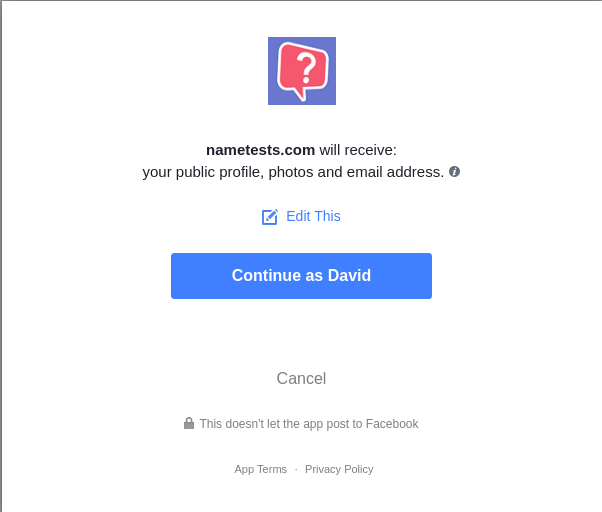
I've seen another request recently where it was "Facebook Profile and Friends". In the case of the Cambridge Analytica efforts, the request was for the full Facebook profile and the Full profile of FRIENDS.
Clicking Cancel on the request for access approval simply returns me to the solicitation page.
Facebook API for login
https://developers.facebook.com/docs/facebook-login - Documentation overview
https://developers.facebook.com/docs/facebook-login/overview/ -- Use cases and user experience. The basic idea is that a website author can use this to simplify their task of authenticating users. By having someone authenticate via their Facebook account, then the website author can rely on the fact Facebook has pre-authorized that person.
https://developers.facebook.com/docs/facebook-login/review -- Reviewing the login process and the requirements
https://developers.facebook.com/docs/facebook-login/review/requirements -- Requirements
https://developers.facebook.com/docs/facebook-login/userexperience/ -- Presenting a great user experience.
That section focuses mostly on providing an enticing user experience that will tend to cause the user to follow through with the signup process. Down at the bottom a little is said about data policies and asking for permissions, but only after lots of information about creating an enticing process
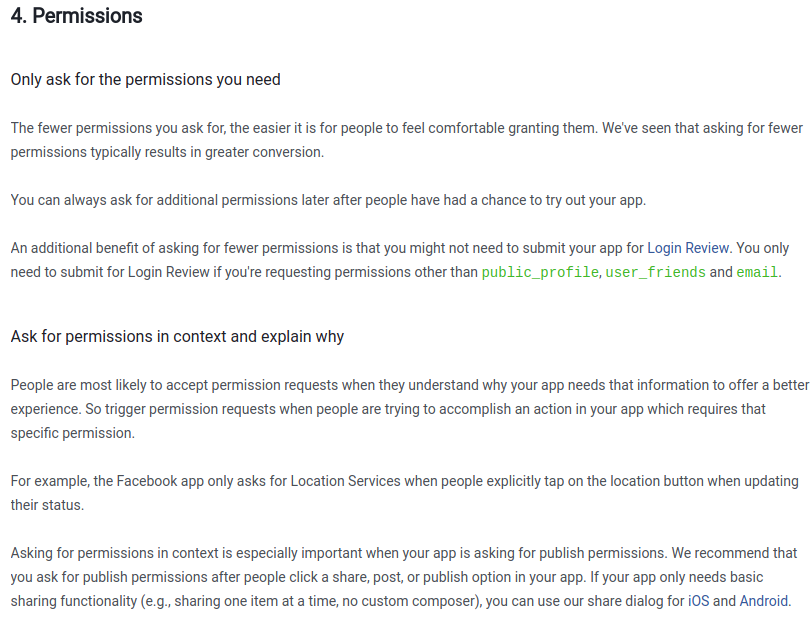
https://developers.facebook.com/docs/facebook-login/permissions -- The permissions system. There is a wide range of granular permissions to request. Some app developers ask for full permissions.
https://developers.facebook.com/docs/facebook-login/best-practices -- Best practices, which is more a simple review of the above.