; Date: Fri Oct 27 2017
Late in the 2016 election, news broke that Trump Campaign servers had been communicating through an arcane channel with servers owned by Alpha Bank. Alpha Bank is closely connected to Russian President Vladimir Putin and his cronies, and has been tied to Russian Oligarch money laundering activities. The news came amid other allegations of collusion between Trump and the Russians, and is routinely mentioned by Journalists like Rachel Maddow as part of the rationale for the Trump-Russia-Collusion story. The news broke in a Slate article that detailed work by a group of Internet Security researchers. The article discusses some kind of database of DNS records that somehow describe the architecture of a set of Internet services that somehow describe a pattern of communication between Trump's organization and Alpha Bank. Reading between the lines of the article, the data source has to be someone with access to primary DNS servers who can gather logs of DNS queries.

Unfortunately
the Slate article doesn't give enough information to understand what the heck they're talking about. I know a fair amount about the Domain Name System, and what's published in the Slate article isn't enough to make sense of it. However, the Slate author did consult with several big names in the Internet, so I'd tend to give some benefit of the doubt.
I'll also note that during 2017,
as detailed in an Intercept report on October 27, 2017, Alpha Bank has enlisted the help of a high-powered law firm, Kirkland & Ellis LLP, to threaten lawsuits and otherwise threaten one of the researchers named in the Slate article. The goal seems to be uncovering the identity of Tea Leaves, a researcher hiding behind a pseudonym in the Slate article. Alpha claims nothing untoward is occurring between it and the Trump administration, and that instead the traffic noted by the researchers is nothing more than SPAM from Trump Hotels.
As The Intercept notes, this sort of investigative work is very important because of the prominent role of the Internet. Journalists and security researchers need the freedom to collect the sort of data shown here, and analyze its meaning.
The possibility exists that top players in political and business empires could be colluding with each other through private Internet-based communication channels. Researchers with the technical chops to uncover such communication must have the freedom to conduct that research.
Questionable Domain Name System queries indicates questions about Trump and Alpha Bank connections
According to the Slate article:
Computer scientists have built a set of massive DNS databases, which provide fragmentary histories of communications flows, in part to create an archive of malware: a kind of catalog of the tricks bad actors have tried to pull, which often involve masquerading as legitimate actors.
Several things written in the Slate article make it clear the author barely understands the technical meaning of what is being reported. This is an example.
The Domain Name System (DNS) contains several sorts of identifying information. The primary purpose is the A record, which is what connects a name like www.cnn.com to an IP address, like this:
$ ping www.cnn.com
PING turner-tls.map.fastly.net (151.101.41.67): 56 data bytes
64 bytes from 151.101.41.67: icmp_seq=0 ttl=55 time=1737.048 ms
DNS records can contain other information such as service descriptions. For example a technique popularized by Apple involves a DNS server for the .local domain. Any computer can advertise itself with a .local domain that is visible only to the local network segment, making it easier for a human to use local services such as printers. The services describe themselves in DNS records that can be dynamically looked up by software needing to access the service.
The Tea Leaves guy is described as "a pseudonym that would protect his relationship with the networks and banks that employ him to sift their data". In July 2016 he found "malware emanating from Russia" with a destination naming a domain containing the word trump. The indications were that "a bank in Moscow that kept irregularly pinging a server registered to the Trump Organization on Fifth Avenue."
The problem is the word "pinging" probably does not refer to the ping protocol I showed a couple paragraphs back. It probably means some kind of communication of data, but the article doesn't describe what is inside that communication. The article discusses that problem -- the researchers are tracking DNS records, and cannot access the actual communication. Supposedly the existence of these DNS records show communication is happening.
Their initial fear - that the records indicated a malware attack - were quickly proven false. Instead it showed a pattern of activity indicating "conversations that began during office hours in New York and continued during office hours in Moscow".
The Domain Name for the server at the Trump end had been first registered in 2009, and was associated with "consumer marketing campaigns". Meaning, that the domain name was used to send out bulk mail campaigns, presumably related to Trump hotels. Specifically, https://who.godaddy.com/whoisstd.aspx?domain=trump-email.com or trump-email.com.
Attempts to access servers connected to this domain resulted in errors -- in a way that made researchers believe the servers were configured to accept connections from a limited set of IP addresses. One would do this to create a secure channel usable by a limited set of people.
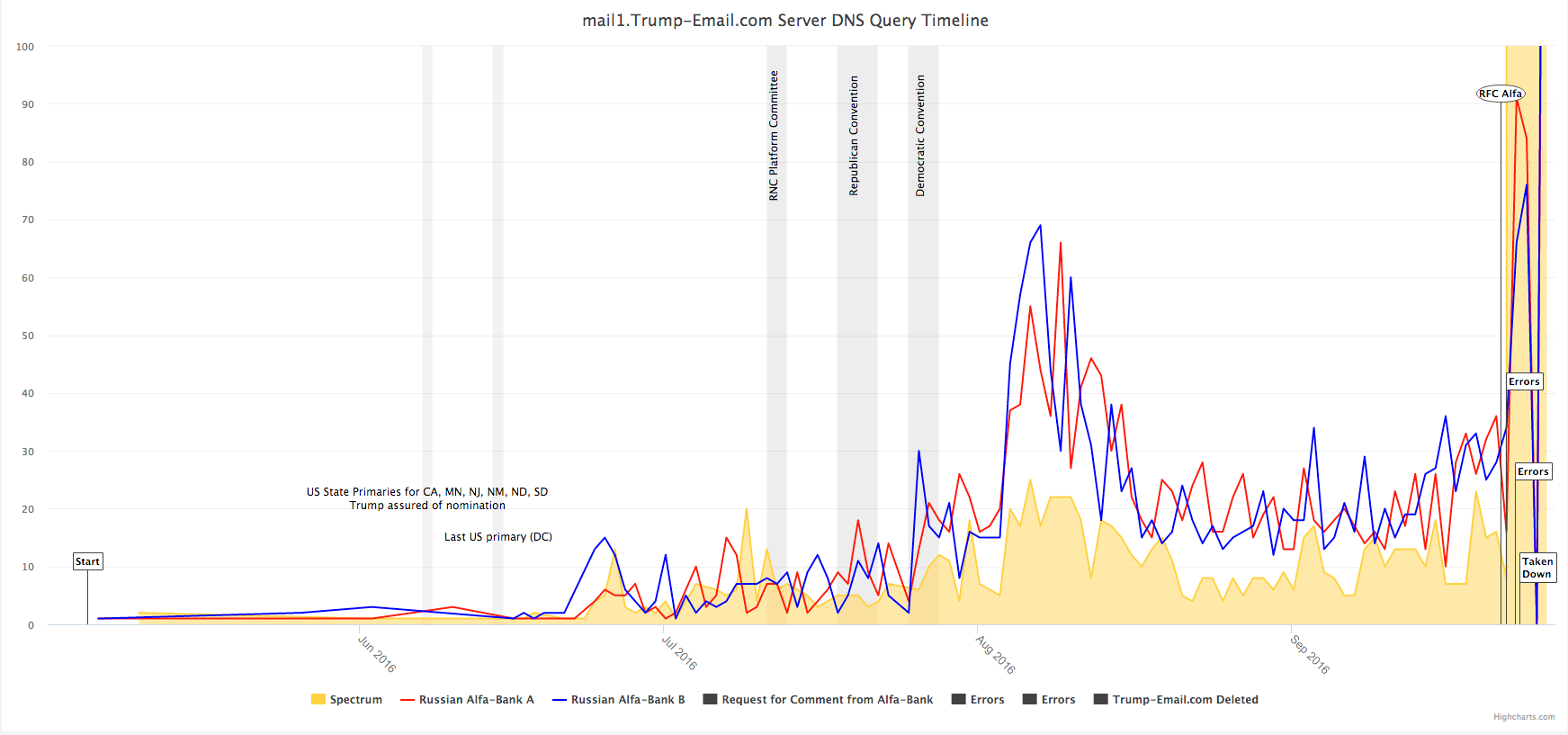
This image is presented as a piece of evidence gathered by these Internet researchers. It shows a pattern of queries for the domain name mail1.trump-email.com made by IP addresses associated with Alpha Bank. The image comes from a Wordpress account containing exactly one posting connected to "Tea Leaves".
That this is presented as evidence, gives us a clue to the data source for the claims in the Slate article. To gather queries for DNS names requires sufficient access to principle DNS servers that one can capture logs of DNS queries.
That is -- when you type in www.cnn.com in your web browser, the computer doesn't know the corresponding IP address to contact. Instead it queries the DNS system. The DNS system is a shared cooperative system running on DNS servers spread around the world. The "root" servers are the central point in the system, and handle any queries that cannot be answered by a local DNS server such as the one built into your WiFi Router. Someone with administrator access to the "root" servers could have an interesting database of which IP addresses are querying for what domain names.
During September and October 2016, the existence of this domain name and the traffic was starting to be publicized. Alpha Bank was contacted by Journalists, and within a few hours the trump-email.com domain name was deleted from the "Trump authoritative name server zone," meaning that an IT administrator in the organization tried to erase the domain from the Internet. The spike in traffic shown here is a result servers trying to resend messages that are being rejected because the domain name no longer exists.
A few days later, a new domain name trump1.contact-client.com was created pointing to the same IP address(es).
Critiques
A
followup article on Slate goes over some flaws and other updates in the original article.
First - the server in question would not have been directly owned by the Trump Campaign or even by Trump's other businesses. It is common practice for a service provider to allow folks to assign a domain name to the service. The domain name in this case is owned by some Trump organization, but the IP addresses it points to correspond to the service provider.
In this case the IP addresses correspond to servers operated by Cendyn, "a vendor that organizes email marketing campaigns for hotels and resort". That's consistent with the denials from Alpha Bank and the Trump Campaign, that the DNS traffic logs were the simple byproduct of spam emails sent by Trump Hotels. Except - why did Journalist queries to Alpha Bank suddenly make the Trump IT organization yank the domain from its DNS servers?
Second - the DNS logs cannot be a complete record of queries for that domain name. The nature of the Domain Name System is that it's highly extremely decentralized. It's not that all DNS queries go to a central server. It's that queries go out to the nearest server, which turns around to ask higher authorities for any data it does not posess. That means there's no central log of all DNS queries, and therefore the data presented in the original Slate article was skewed.
Why would Cendyn (a 3rd party) be involved with establishing a back-channel communications portal between the Trump campaign and Russians? Isn't that a risky maneuver? It's a 3rd party, that presumably can act on its own. And are the services offered by that 3rd party (sending bulk email) useful to anything related to collusion? Why not set up something using raw IP addresses?
Intercept says a dossier and other data had been passed around to several news organizations, including The Intercept. While Slate decided to run an article, others did not, and the Intercept says they didn't because the claims did not add up.
The simplest explanation is that the traffic in question is the simple result of e-mails advertising Trump Hotel properties. Several bits of proof are offered by The Intercept to support that claim.
Namely, a good practice is to attempt a "reverse connection" to the originating e-mail server to verify it is a real server.











