; Date: Mon Aug 05 2019
Tags: Apple »»»»
Apple cannot be happy about the Hackintosh community. These people are using Mac OS X, that Apple provides for free, but on hardware that Apple does not manufacture. Obviously Apple's Mac OS X is "free" as a way to incentivize sales of Apple computers. So far Apple's attempts to kill off Hackintoshing have failed, because the Hackintoshers have ingenious worked around everything Apple has done to stop them. But the T2 Security Chip may mean the end of the road.
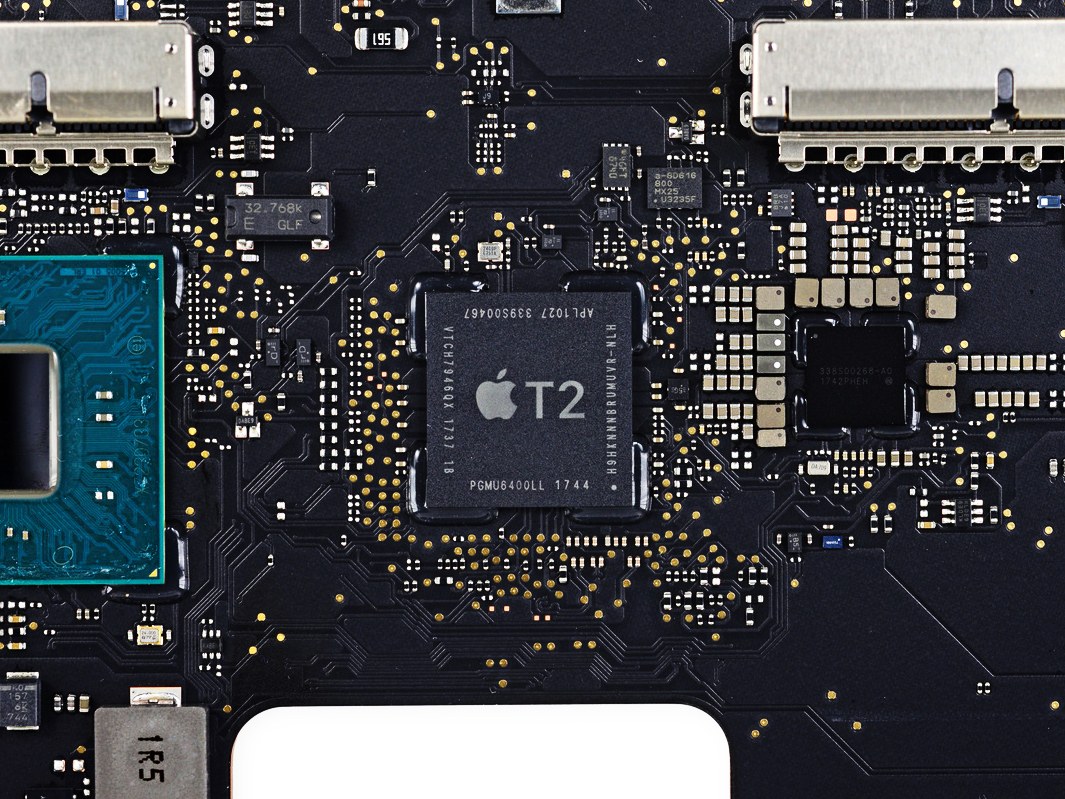
Let's quickly review some aspects of the T2 Security Chip (see What is the T2 Security Chip on modern MacBook's)
- The Secure Enclave on the T2 Security Chip contains a chain of encrypted certificates that are custom-generated for each chip during its manufacture.
- By default the T2 chip encrypts all data on the storage device using those keys.
- Encryption keys stored in the Secure Enclave cannot be retrieved by any means from outside the T2 chip.
- The T2 chip serves many functions including the SATA controller.
The bottom line is that for a computer with the T2 Security Chip, the storage device is encrypted in a way that prevents the data from being readable on any other machine.
Mac OS X currently runs fine on computers that do not have T2 Security Chips. Before Apple developed the T2 chip, they sold many many computers (like the 2012 MacBook Pro on which I'm typing this article) that obviously did not have this chip. Mac OS X still supports those systems but we should expect Apple to End of Life them within a few years.
The attached video goes over some highly extremely technical details of hardware in the latest MacBook Pro's. The video is extremely technical, presented by someone who does hardware level repair of MacBook logic boards every day, and who knows the circuitry like the back of his hand.
What he shows is that the T2 Security Chip has taken over functions that are normally supplied by Intel system management chips. For example he traces a power line that is supposed to be generated by the CPU, but is instead generated by the T2 Security Chip. The pin from the CPU is simply connected to ground rather than to the wiring it should be connected to.
It's presented quickly enough you may come away from the technical gobbledygook thinking "so what"?
This video implies that Apple is preparing for the way for Mac OS X to explicitly require being executed on a computer containing a T2 Security Chip.
This chip already acts hand-in-hand with Mac OS X. For example the chip generates encryption tokens that cannot be accessed from anywhere other than this chip, and are unique to each individual chip. The T2 chip prevents a computer from booting if the Mac OS X or the kernel extensions (KEXTS) etc are not validated by encryption tokens contained in this chip.
It's not hard to imagine a future Mac OS X to absolutely require that it be executed in the context of security tokens generated by a T2 chip. Or maybe it will be a T3 chip by that time?