; Date: Thu Aug 01 2019
Tags: Mac OS X »»»»
At some point Apple designed the MacBook's and MacBook Pros with the T2 Security Chip. It's just there, and supposedly it's a good idea. But like all things, it's useful to know what the chip does, and more importantly why Apple designed this chip into the system. Supposedly it increases security, otherwise why is it called the Security Chip, but is there another purpose. Apple is famously tight-lipped about its roadmap, so what if this is a game of multi-dimensional chess where the T2 chip is a harbinger of something else?
What follows is a summary of a document from Apple, Apple T2 Security Chip Security Overview, that gives a fairly decent description of the various functions of the T2 Security Chip. The chip does a lot of things, as evidenced by this bullet point list provided by Apple:
- Secure Enclave coprocessor
- Foundation for APFS encrypted storage, secure boot, and Touch ID
- Integrates the system management controller, image signal processor, audio controller, and SSD controller
- Dedicated AES hardware engine - for encrypted APFS
- Hardware root of trust for secure boot - ensures that the lowest levels of software aren’t tampered with and that only trusted operating system software loads at startup
- On Mac computers with Touch ID and the T2 chip, the Secure Enclave also secures Touch ID.
- On all Mac portables with the T2 chip have a hardware disconnect that ensures the microphone is disabled when the lid is closed.
The short of it is that the T2 Security Chip sits in the middle between all kinds of interactions inside the computer. Its primary function is encryption and ensuring that operating system and device driver code comes from a trusted authenticated source. While Apple is claiming that everything is fine, nothing amiss, we should take that claim with a grain of salt. We should look at this questioning whether Apple has a hidden agenda in play.
Secure Enclave
The Secure Enclave is a coprocessor fabricated within the system on chip (SoC) of the Apple T2 Security Chip, built solely to provide dedicated security functions. It protects the necessary cryptographic keys for FileVault and secure boot, and is also responsible for processing fingerprint data from the Touch ID sensor (if present) and determining if there’s a match.
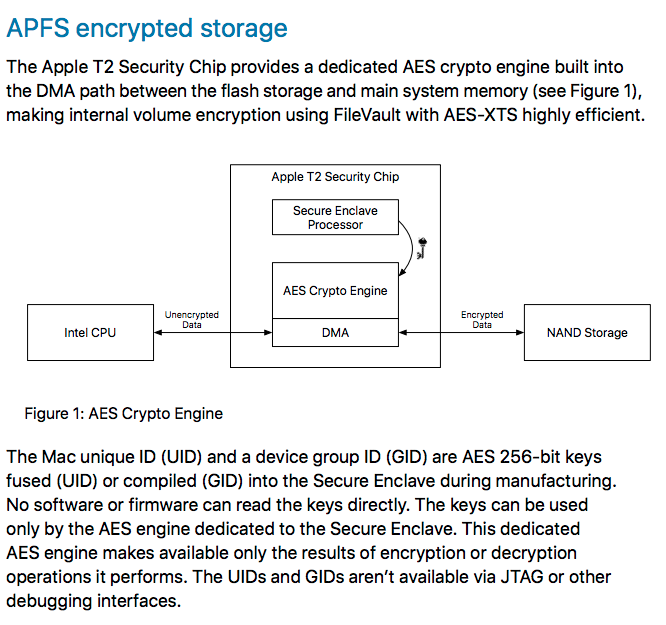
This says that there is hardware encryption of file-system data using secure encryption keys that cannot be accessed from outside the chip. The document goes on to say the UID is unique to the device, and that the encrypted key hierarchy is stored completely within the chip. The result is that a storage device cannot be accessed by any other computer.
FileVault became available with Mac OS X 10.3 and later. It uses AES-XTS encryption for "full volume" data protection. On systems with the T2 Security Chip, FileVault leverages the on-board encryption.
Another effect for such machines is that user credentials are required during the boot process.
Lacking "valid login credentials or a cryptographic recovery key" the APFS volume remains encrypted and therefore inaccessible.
Goals:
- Require the user’s password for decryption.
- Protect the system from a brute-force attack directly against storage media removed from Mac.
- Provide a swift and secure method for wiping content via deletion of necessary cryptographic material.
- Enable users to change their password (and in turn the cryptographic keys used to protect their files) without requiring re-encryption of the entire volume.
Even if FileVault is not enabled, the APFS volume is still encrypted.
The document does not describe what a cryptographic recovery key is. Maybe this is a magic cryptographic token that Apple repair folks can use?
Secure Boot
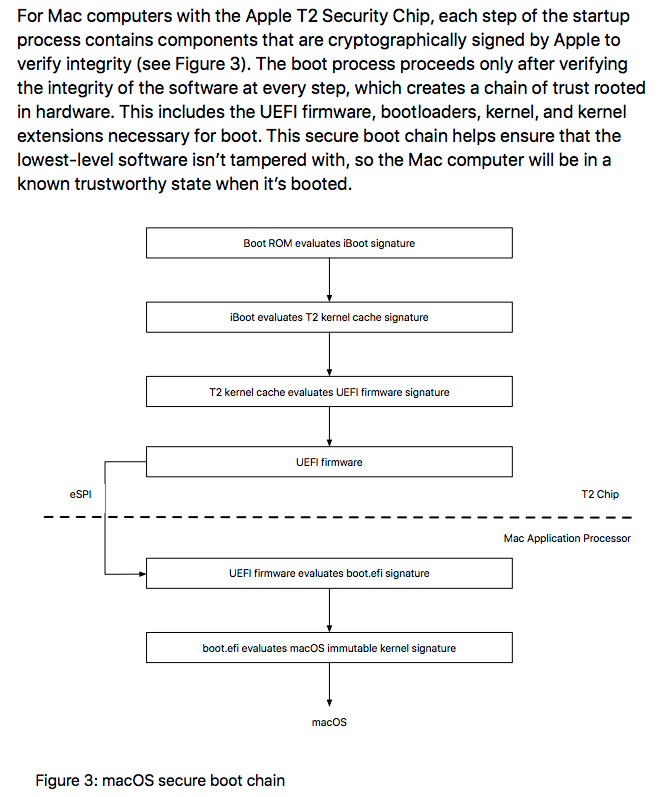
The document goes on to describe the boot process. A Boot ROM is generated during chip fabrication, which sounds like a unique cryptographic certificate is generated for each T2 chip. The certificate is used to verify the iBoot bootloader. That in turn verifies the kernel and kernel extensions.
It looks like the result is that only verified kernels can boot a Mac with the T2 Security Chip. However the document also says Secure Boot can be configured for one of three modes: A) Full Security, B) Medium Security, and C) No Security
Touch ID
The role of Touch ID is to allow using a fingerprint instead of a password, in many cases. Any of us who have a recent model iPhone are familiar with TouchID since we can use that to log in to the iPhone and use it in many cases to authenticate against apps or services.
On a Mac, touching the Touch ID sensor can unlock the computer, and enable authentication against iTunes, App Store, Book Store, and much more.
The Touch ID system doesn't store fingerprint images. Instead it computes a mathematical model of the fingerprint. A key claim by Apple is:
This representation is encrypted, stored on the device, and protected with a key available only to the Secure Enclave.
We know from an earlier section that the Secure Enclave is part of the T2 Security Chip, and contains digitally signed certificates and other authentication keys. The keys are derived from one generated at the manufacturing date of the chip.
Getting back to the Touch ID, Apple claims:
The fingerprint data is used only by the Secure Enclave to verify a match with the enrolled information. It can’t be accessed by macOS or by any apps running on it. It’s never stored on Apple servers, it’s never backed up to iCloud or anywhere else, and it can’t be used to match against other fingerprint databases.
A password is required in these scenarios:
- The device has just been turned on or restarted.
- The device hasn’t been unlocked for more than 48 hours.
- The password hasn’t been used to unlock the device in the last 156 hours (six and a half days) and a biometric hasn’t unlocked the device in the last 4 hours.
- The device has received a remote lock command.
- After five unsuccessful attempts to match a fingerprint.
Hardware microphone disconnect
It's possible for miscreants to reach into a computer and turn on the microphone to commit some kind of badness. It's not just the microphone but the camera. This should be scary for all of us. There's so much concern that it's possible to buy a sliding cover for laptop cameras, so that the camera can see only when you uncover the camera.
Anyone concerned about unwanted eavesdroppers should be interested here.
What Apple says is:
All Mac notebooks with the Apple T2 Security Chip feature a hardware disconnect that ensures the microphone is disabled whenever the lid is closed. On 13-inch MacBook Pro and MacBook Air computers with the T2 chip, this disconnect is implemented in hardware alone, and prevents any software—even with root or kernel privileges in macOS, and even the software on the T2 chip—from engaging the microphone when the lid is closed. (The camera is not disconnected in hardware because its field of view is completely obstructed with the lid closed.)
References
Source:
Apple T2 Security Chip Security Overview











