; Date: Tue Jan 02 2018
Tags: Internet Privacy »»»»
Your email account is the skeleton-key to your life, since all kinds of services send emails to verify this and that. Protecting your email account(s) is, then, vital to securing your online life. Since Google's gmail is perhaps the most popular email platform, we'll look at an effective way to secure your gmail account(s). Namely, 2-factor authentication means logging in requires access to not just your password, but to a second device - such as your cell phone.

Google has fairly comprehensive support for 2-factor authentication. Simply go here:
https://myaccount.google.com/security#signin
That's the portion of your Google Account page concerning the sign-in process. Another way to find this page is to start while logged-in to a Google service like Gmail, or YouTube, and to click on the avatar icon in the upper right corner of the window. This is the menu which allows switching between logged-in accounts, AND it gives easy access to your Google Account home page.
Namely:
https://myaccount.google.com/ That page includes a box labeled "Sign-in and Security" which leads to the page linked above.
On
https://myaccount.google.com/security you'll find a box labeled "2-Step Verification". If you've not turned it on, the word "Off" will appear. In any case, click on that box.
You'll end up here:
https://myaccount.google.com/signinoptions/two-step-verification
As the URL implies, this is the page to enable the 2-step login verification process.
By the way, folks with GSuite accounts are unable to use the 2-step login verification process. I have several GSuite accounts, including my primary e-mail address. I've just checked with two of them, and neither offer 2-step login verification as an option. But every one of my Google Accounts for the "
google.com" domain do offer 2-step login verification.
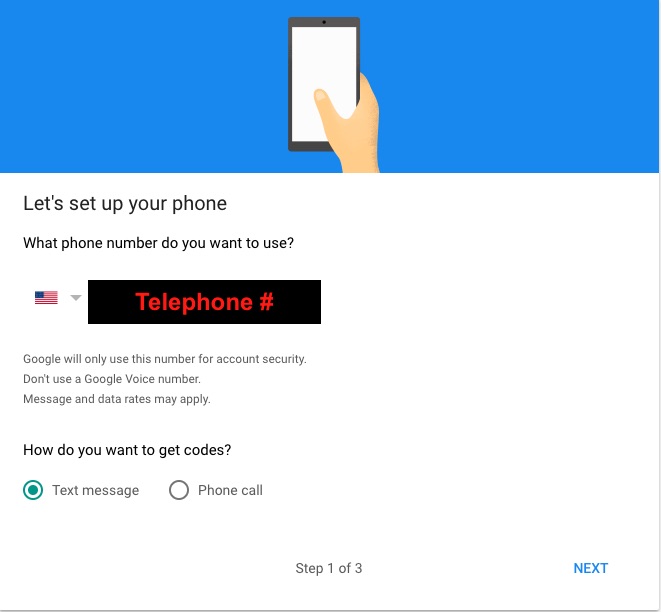
At this point the default is that Google will send you a text message every time you sign-in to a Google account. The improvement is that a miscreant has to have your cell phone in order to log-in to your account. It's not enough to figure out your password, but they must also steal your cell phone.
That of course makes your cell phone a critical device you must protect at all costs - and a single point of failure which could block access to your accounts. But --- Google offers some alternate methods for authenticating that decreases the criticalness of your cell phone.
An issue which weighs heavily on me is that I sometimes travel to other countries. While there, I try to not use my US cell phone number because AT&T charges through the nose for foreign usage. And remember that Canada is a foreign country (to the USA) and you'll pay through the nose for the privelege of using your AT&T cell phone in Canada.
If I'm staying in the country for a long enough period, I'll get a local SIM card and pop that into my cell phone. With a foreign SIM card in my phone, I no longer have access to my USA phone number because it's assigned to the AT&T SIM card. That, in turn, means that those accounts which send a text message for 2-factor authentication are now a liability -- because if my cell phone isn't answering for that phone number, I'll never receive the text message, and I won't be able to log-in to the account.
Let's go over the alternative authentication methods offered by Google
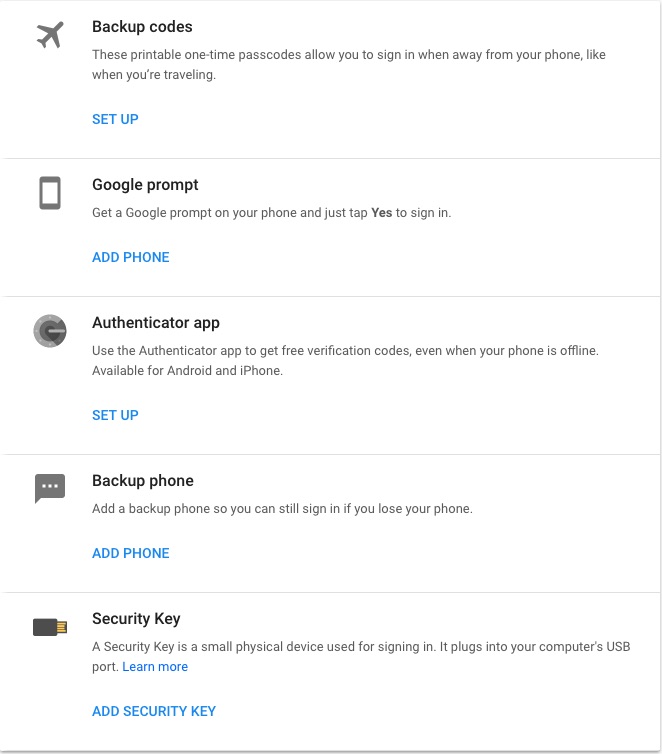
Backup Codes Google provides you with a list of code numbers you can print out and carry with you. Each are a one-time passcode. I suggest turning this off until you need to make an overseas trip.
Google Prompt This is an application installed on the cell phone to which you can tap Yes to authenticate yourself. I started to set this up, but the application claimed it needed to track my web browsing and other activity, so I declined this one.
Authenticator App This is another application installed on the cell phone. You register your phone with the Google account by scanning a QR code. Anytime you're requested to authenticate with Authenticator, you run the app, and it shows a constantly updated code number. Simply enter the code number into the sign-in form, and you're authenticated. I am using this method.
The only downside to the Authenticator app is if you have multiple services using it. The Authenticator app is open enough that any company can utilize it - for example I have two AWS account entries in my Authenticator app. Plus, I have several Google Accounts, and each one is a separate Authenticator entry. Bottom line is that it'll be easy to have enough services registered with the Authenticator app to complicate its use.
Each service listed in Authenticator generates a separate Authenticator code. Therefore you could easily have a dozen such services, or more, and therefore have a dozen or more Authenticator codes. You have to be careful to select the correct code for the service you're authenticating with.
Backup phone This would be a second phone number that can be used. For example, once you arrive in the foreign country and get the local SIM card, enter its phone number here.
Security Key A physical device that offers security codes. I don't have one for Google, but have used such things for authentication with workplace internal networks, and it's fairly easy to use so long as you remember to carry that security key dongle at all times.











