; Date: Thu Oct 11 2018
Tags: Department of Defense »»»» Cybersecurity »»»» Weapons Systems »»»»
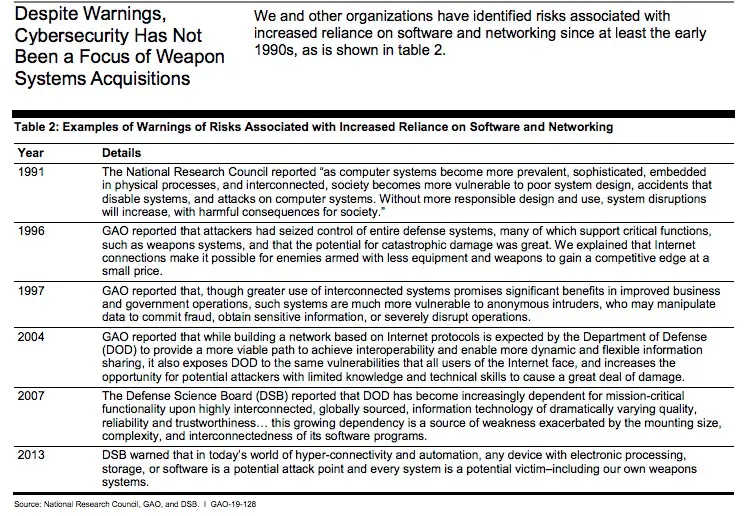
It's a brave new world. Consider a military warplane flying into battle, or a warship engaged in a sea battle, or a tank battle. In the past that military equipment was standalone, with communications limited to voices speaking over the radio. Now such equipment is connected in a digital communications network using the same technology as the Internet. A recent US Government Accountability Office report found these systems are vulnerable to attacks due to weak cybersecurity. One wonders if the result might be an airplane plummeting out of the sky, or a tank stopping in its tracks, or the guns on a warship going silent, during combat, because the adversary hacked into critical systems.
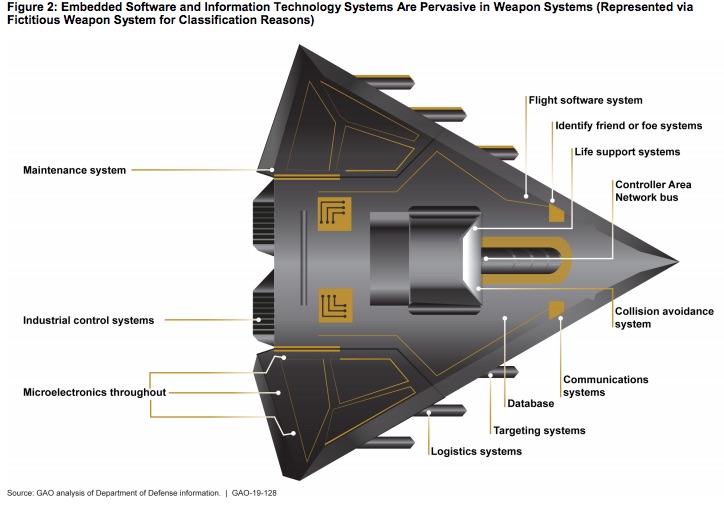
Over the past few years Internet-connected equipment has grown more common. The phrase "Internet of Things" (IoT) applies not just to consumer gizmos like WiFi-connected security cameras or baby monitors, but to all kinds of critical infrastructure. Some of that critical infrastructure is in the military.
Remember that the US Department of Defense funded the development of the technologies underlying the Internet. That project began in the 1960's and was tasked, in part, with developing a command and control system for the Military that could withstand a nuclear attack. Fast forward 50 years, and the US Military has a few decades of experience with using the Internet in the conduct of its business.
Historically the US Military had a parallel Internet called MILNET. When I got on the Internet in 1986 or thereabouts, "The Internet" had yet not been coined and instead you had ARPANET (the open public TCP/IP based Internet primarily for Universities) and MILNET (the semi-closed TCP/IP based Internet for the US Military). Access to MILNET was always semi-closed just as today every large corporation has a private TCP/IP based network that is closed to access by the general public. Therefore the military systems we're about to describe are not on the open public Internet, but they are still connected to a wide area TCP/IP-based communications system.
The
GAO Report is based on classified research, with the public report having various details obscured. We don't know the precise weapons systems etc, just that GAO researchers were able to hack into various weapons systems while they were in use without knowledge of the operators.
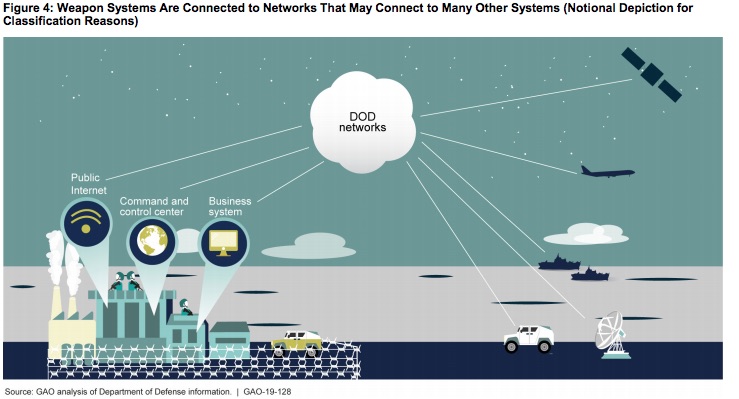
As one might expect, US military equipment around the world partakes in a global communications system. The US Military has an extensive satellite network that not only serves as a communications backbone, but contains imaging and other sensors. Communications through this system is ubiquitous in the military. Because it is a TCP/IP-based digital network, it doesn't just carry voice communications but any kind of data service you can imagine.
The report says:
These connections help facilitate information exchanges that benefit weapon systems and their operators in many ways—such as command and control of the weapons, communications, and battlespace awareness. If attackers can access one of those systems, they may be able to reach any of the others through the connecting networks. Many officials we met with stated that including weapon systems on the same networks with less protected systems puts those weapon systems at risk. Furthermore, the networks themselves are vulnerable. DOT&E found that some networks were not survivable in a cyber-contested environment and the DSB reported in 2013 that “the adversary is in our networks.”2
A key observation is this:
For example, many weapon systems use industrial control systems to monitor and control equipment, and like computers, they include software. Many weapon systems use such systems to carry out essential functions. For example, a ship may use industrial control systems to control engines and fire suppression systems. According to NIST, industrial control systems were originally designed for use in trusted environments, so many did not incorporate security controls. Government and industry reports state that attacks on these systems are increasing. However, DOD officials said that program offices may not know which industrial control systems are embedded in their weapons or what the security implications of using them are.
I believe this is referring to the equipment used in SCADA systems - for example to implement factory automation, warehouse automation, or utility company automation. The typical communication protocols (DNP3, MODBUS, etc) were designed in the 1960's and 1970's and simply do not have a security model. The assumption was the control system would be on a network not connected to anything else, and therefore physical access would be required, and therefore preventing physical access is a sufficient level of security.
In the modern age all systems are being connected to each other and therefore those assumptions are ...er... quaint.