; Date: Mon Apr 24 2017
Tags: Security »»»» Internet of Things »»»» Botnets »»»»
The last few months has seen escalating botnet activity on the Internet. The botnet operators are targeting non-existent security in certain Internet of Things devices. Some devices, like wireless security cameras or baby monitors, are not only connected to the Internet, but have gaping security holes. Using those holes, botnet operators have ammassed vast flotillas of Internet devices that can be commanded to attack targets on the Internet. Last fall several attacks, larger than any previously seen, attacked several large sites and even brought down critical Internet infrastructure on a few instances. The Brickerbot appears to be a Botnet purposed with destroying those malicious botnets. One hopes the cure is better than the illness.
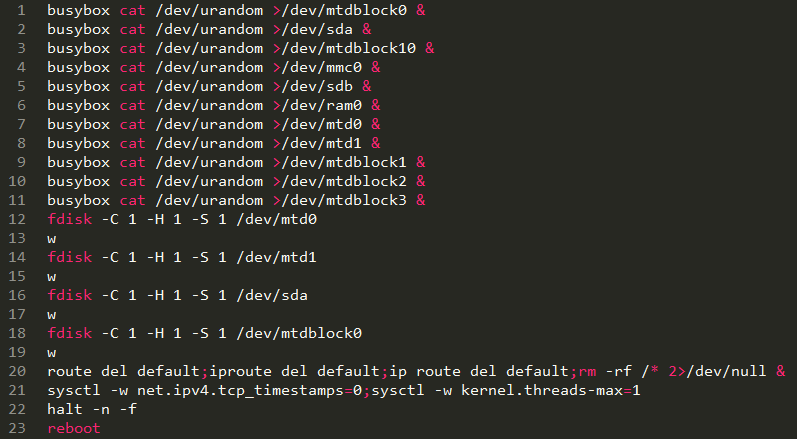
According to ArsTechnica, [ArsTechnica1] Brickerbot breaks into Internet of Things devices, just like the malicious botnets. What's different is they permanently disable the device using the commands shown above.
The effect of those commands is to wipe out any disk or flash storage device attached to the computer, to reformat the disks, to delete Internet routing configuration, and then finally reboot the system. Once rebooted the system is incapable of doing anything, and a factory reset is unlikely to return its functionality. In other words, it "bricks" these devices.
According to Radware, [Radware1] the Brikerbot attacks are coming from a limited set of IP addresses that also appear to be Internet of Things devices running Busybox and the Dropbear SSH service. Busybox is an open source utility providing Unix-like command-line tools, and is popular among Internet of Things device makers.
The Brickerbot attack uses the same the same attack vector as the Mirai botnet. Ergo, one assumes the Brickerbot operators are targeting the destruction of Mirai.
The owners of permanently bricked IoT devices might not appreciate the subtleties here. They're the ones who'll have to foot the bill to pay for replacement devices.
ICS-CERT [ICS-CERT] says they're contacting IoT device makers to mitigate the attacks. The actions include changing default credentials on target devices, and disabling Telnet access.
The bottom line question - is Brickerbot a good thing, or a bad thing? Is it a "nasty piece of software"? It destroys the functionality of IoT devices. The side effect is to deny those IoT devices from being used by Mirai, arguably a desired result. But, the basic result is to destroy the devices, causing harm to device owners around the world.